
Microsoft has updated a utility designed to test applications that call the Microsoft Graph or other 365 APIs, to add guidance when developers have inadvertently granted unnecessary permissions to logged in users.
The company has been low-key about its Developer Proxy tool, currently in “community preview”, yet it has good potential to improve the security and resilience of custom applications which use Microsoft Graph, an API for the various services that make up the 365 platform. The tool runs on the developer’s machine – Windows, Mac or Linux – and intercepts requests to Microsoft APIs. By default, it introduces errors, so that there is a 50 percent chance of any request failing with a supported error code, a form of chaos engineering that helps when coding an application to behave nicely when 365, or possibly the local network, is misbehaving.
The most common use of Microsoft Graph is for authentication. Rather than creating a separate user database for a business application, it makes sense to use the existing corporate log-in, and if that is Azure Active Directory, often synched with on-premises Active Directory, this requires a Microsoft Graph call.
The downside of using Azure AD authentication though is that careless implementations can introduce security issues. For example, it is no use simply checking that a user has authenticated successfully with Azure AD; the application has to restrict access to specific groups in its own tenancy for this to be meaningful.
Another common problem is working out what are the minimum permissions required. Devs or admins faced with errors trying to get an application working can fall into the trap of giving excessive permissions just in case it fixes a problem, and the complexity of Microsoft security makes this more likely.
The new preview of the Developer Proxy includes a plugin to address this. The developer sets the proxy to record requests, and compares the permissions granted with those actually needed by the API calls that are detected. When the recording completes, it reports on the difference. The new feature builds on a previous one which showed what the minimum permissions might be, but did not report on whether the application grabbed more than it needed.
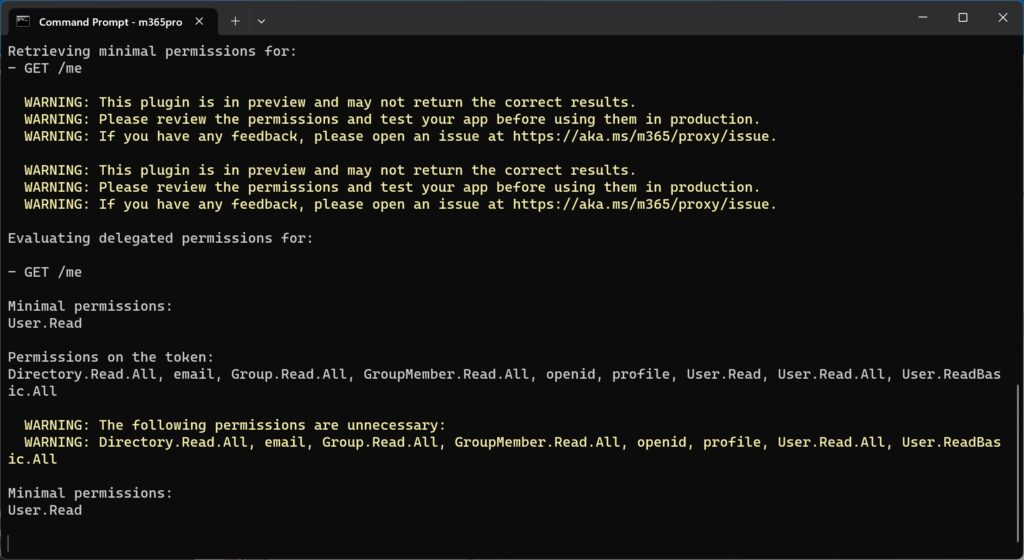
There is a hint that the results may be imperfect. “We’re releasing this feature in preview and will continue to improve its accuracy,” say senior developer advocate Waldek Mastykarz and senior cloud advocate Garry Trinder.
Other features in the Developer Proxy are simulated throttling and rate-limiting, mocking responses of different types, and giving caching guidance. The tool was first developed in September last year, by Mastykarz, Trinder and principal software engineer Gavin Barron, as part of a Microsoft Hackathon. According to the team, “we are working on getting the General Availability (GA) version published within the calendar year 2023.”
